Zscaler Report: Mobile, IoT and OT cyber threats to increase in 2024
New one report Cloud security company ZScaler highlights the growing mobile threats on Android operating systems as well as threats to IoT and OT devices. The findings come as more than 60% of global Internet traffic is now you generated Mobile device and financially oriented mobile threats have increased by 111% compared to last year.
List of mobile malware threats
Contents [hide]
ZScaler’s ThreatLabz found a 29% increase in banking mobile malware compared to last year, with banking malware representing 20% of the total Android threat landscape.
The most active banking malware families to date include:
- VultrWhich is mainly distributed through Google Play Store.
- hydraDistributed through phishing messages, websites and malicious Google Play Store applications.
- ermacDesigned to steal financial data from banking and wallet apps.
- AnatsaAlso known as Teabot
- Tajiralso known as octo
- bondMainly targets cryptocurrency accounts
Most of these banking malware record keystrokes, hijack credentials and intercept SMS messages to bypass multi-factor authentication.
SEE: How to Build an Effective Cybersecurity Awareness Program (TechRepublic Premium)
Spyware threat increased by more than 100%
In addition to banking malware, spyware threats have also increased, with researchers indicating that blocked transactions have increased by 100% compared to last year.
The most popular spyware reported are Spylone, SpinOK, and Spynote.
- spy loan Has the potential to steal personal data from devices, such as accounts, device information, call logs, installed apps, calendar events, metadata, and more.
- spinok Spyware collects sensitive data and files from various locations on the infected device and sends the data to an attacker-controlled server.
- spynoteAlso known as CypherRat, provides additional remote access capabilities so that the attacker can control the execution of software on the mobile device.
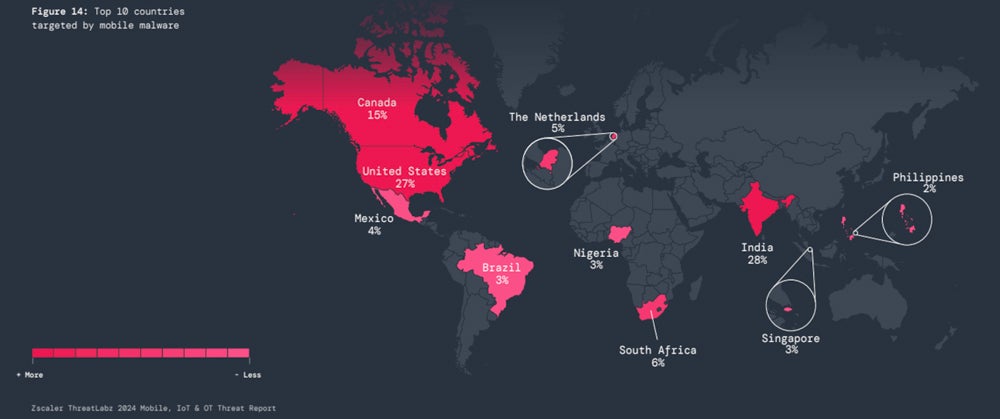
According to ZScaler, most mobile malware targeted India (28%), US (27%), and Canada (15%), followed by South Africa (6%), Netherlands (5%), Mexico (4%) Targeted. Nigeria (3%), Brazil (3%), Singapore (3%) and Philippines (2%).
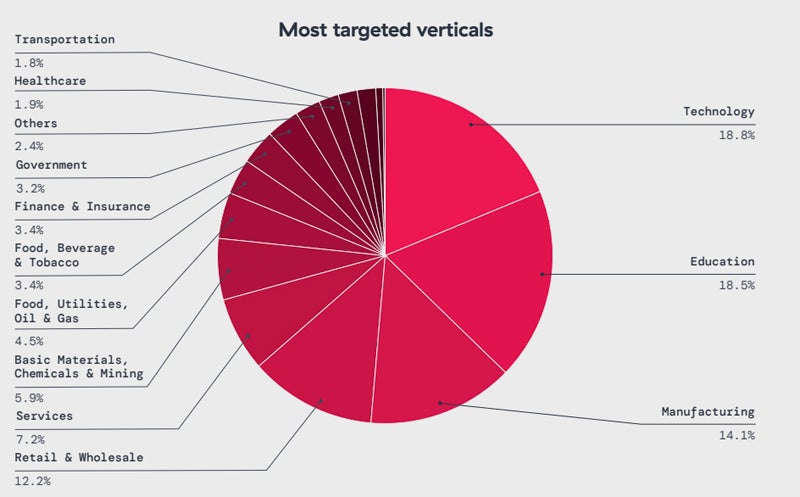
Sectors affected include technology (18%), education (18%), manufacturing (14%), retail and wholesale (12%), and services (7%).
Mobile malware is distributed in a variety of ways. One method involves the use of social engineering techniques. As an example, ZScaler reports that attackers deployed CopyBara mobile malware using voice phishing (vishing) attacks, where the victim received voice instructions to install the malware on their Android phone.
QR code scams are also common, where victims are tricked into scanning malicious QR codes, leading to malware infections or, in some cases, to phishing pages.
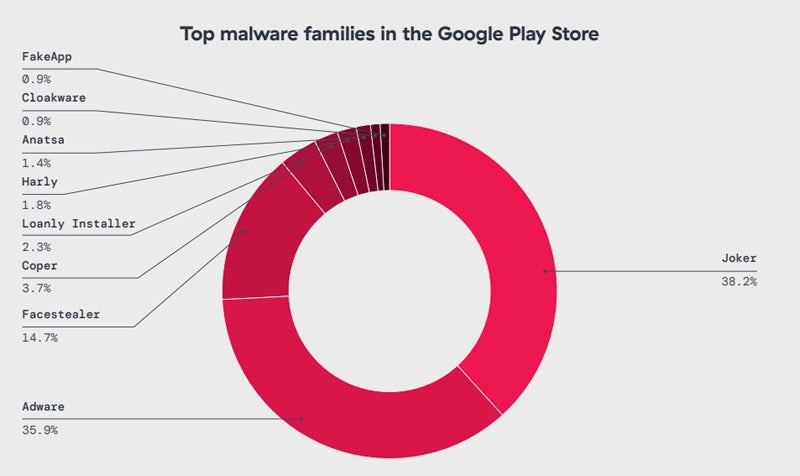
Some malware is also available on Google Play Store. This includes Joker – which silently subscribes to premium services without users’ consent to generate fees – followed by the adware malware type and Facestealer which steals Facebook accounts.
Overall, despite an overall decrease in Android attacks, financially oriented mobile threats have increased by 111% compared to last year.
IoT and OT threats
According to the report, the Internet of Things and operational technology environments are expanding and increasingly being targeted by attackers. Researchers have indicated that the number of IoT devices interacting with them has increased by 37% year-on-year.
IoT malware attacks have increased by 45% in the past year, with routers being the most targeted type of device, with over 66% of attacks aimed at these devices. The leading malware families affecting IoT devices are Mirai (36.3%) and Gafgit (21.2%). Botnets built with these malware on IoT devices can be used to launch large distributed denial of service attacks.
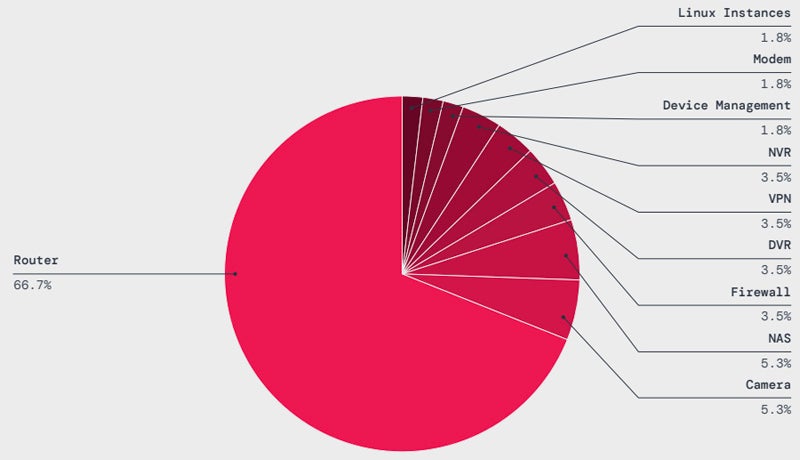
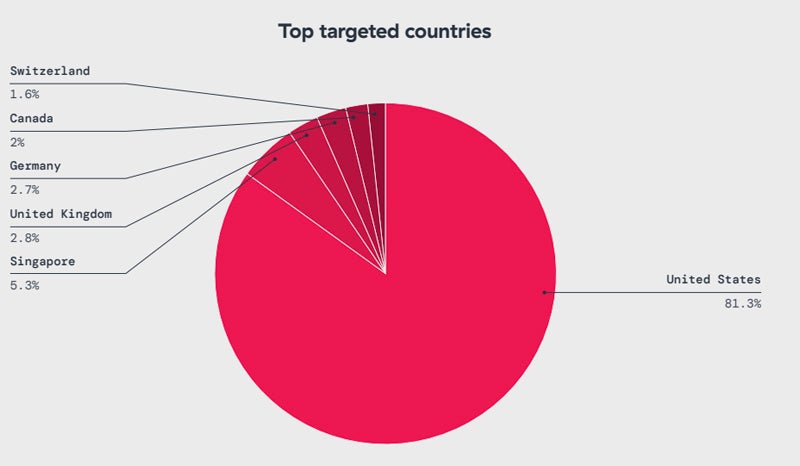
Regarding geographical distribution, more than 81% of IoT malware attacks are aimed at the US, followed by Singapore (5.3%), United Kingdom (2.8%), Germany (2.7%), Canada (2%), and Switzerland (1.6% ).
The top sectors affected by IoT malware attacks are manufacturing (36.9%), transportation (14.2%), food, beverages and tobacco (11.1%).
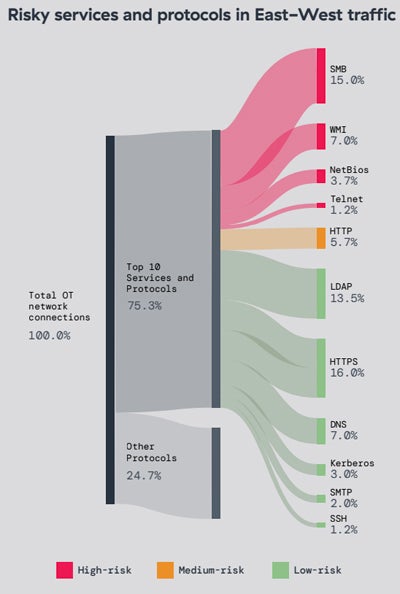
On the OT side, 50% of devices in many deployments use older, end-of-life operating systems. Protocols suffering from various vulnerabilities are also often exposed in OT environments such as SMB or WMI.
As an example, ThreatLabz analyzed the OT content of a large-scale manufacturing organization, which included more than 17,000 connected OT devices across more than 40 different locations. Each site contained over 500 OT devices containing end-of-life Microsoft Windows operating systems, many of which had known vulnerabilities.
67% of global traffic on OT devices was unauthorized or blocked.
What will the future look like?
According to ZScaler, IoT and OT devices will remain the primary threat vectors, while the manufacturing sector will remain the top target for IoT attacks, including ransomware.
ZScaler also suspects that artificial intelligence will increasingly be used to conduct high-quality phishing campaigns targeting mobile users. However, AI will also help defenders automate critical tasks and better prioritize their efforts.
How to protect IoT and OT devices from cyber attacks
To protect against threats on IoT and OT devices, it is essential:
- Gaining visibility over IoT and OT devices is a priority. Organizations need to find, classify, and maintain an inventory of all IoT and OT devices used across their entire environment.
- Keep all systems and software updated and patched To prevent compromise from common vulnerabilities.
- Network logs should be collected and analyzed. Suspicious user account access and system events should be specifically monitored.
- Multi-factor authentication should be deployed whenever possibleAnd the default password and account should be changed or disabled.
- Zero-trust device segmentation should be implemented for IoT and OT assets To reduce data exposure.
How to protect mobile devices from cyber attacks?
To protect against threats on mobile devices, it is important to:
- To protect devices from malware and potential phishing attempts, install security applications on them.
- Any link arriving on a mobile phone, no matter what application, should be carefully examined. In case of suspicious link, it should not be clicked and IT security staff should be informed.
- Unknown applications should be avoided. Also, applications should never be downloaded from third parties or untrusted sources.
Companies should also be wary of applications requesting updates immediately after installation. The application downloaded from Play Store must be the latest version. If an app requests permission to update immediately after installation, it should be considered suspicious and may indicate malware attempting to download additional malicious components.
Disclosure: I work for Trend Micro, but the opinions expressed in this article are my own.
#Zscaler #Report #Mobile #IoT #cyber #threats #increase